In an increasingly connected world, hackers have more ways than ever to attack small businesses and exploit vulnerabilities. However, among the many external threats business owners are aware of, cybersecurity often takes a lower priority against more immediate, visible issues.
Astronaut Neil Armstrong was quoted as saying, “That’s one small step for [a] man, one giant leap for mankind” upon landing on the moon on 1969.
What small systems can your business put in place that make a giant leap forward in cybersecurity protection?
Staying ahead of the game and making a proactive investment in digital security can give your business a leg up on the competition. IBM’s 2020 Cost of Data Breach Report showed the average time to identify a security breach was 228 days, and only 24 percent of cybersecurity professionals surveyed by Ponemon place a concerted focus on prevention strategies. But the cyber threat – and the need for proactive prevention – is only growing, as more than 37 billion online records were exposed from hacks in 2020, more than twice as many were exposed in 2019.
Remaining vigilant and informed is one of the most effective ways to protect your assets, your team and customers, and your entire business. With so many threats to consider, what are the most common ways hackers look to infiltrate small businesses?
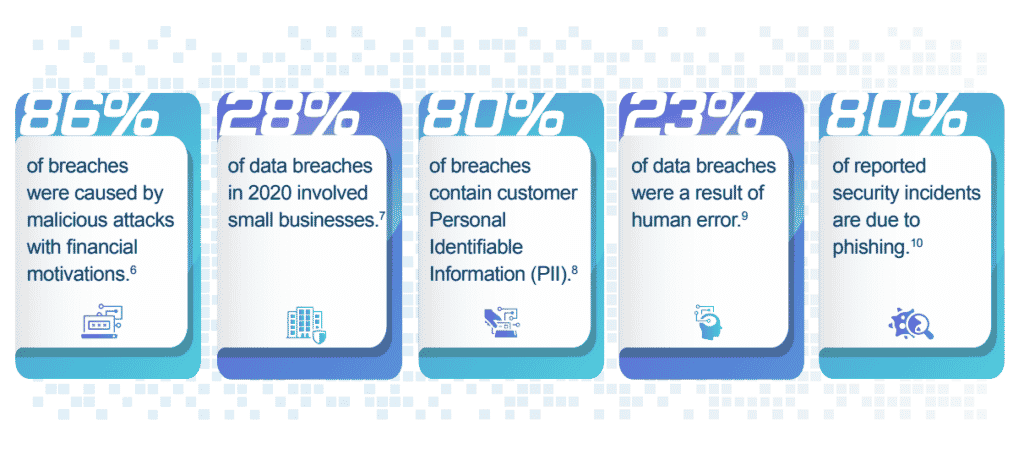
Three Common Cyberattack Targets in Small Businesses
- Targeting Customer Records: One of the most important things to protect are customer data records, which include names, dates of birth, and other personally identifying details. These details are extremely valuable to hackers or criminals who, either use them personally or sell them on to someone who will. Many regions have strict laws and guidelines about how this information must be stored, accessed and protected. Failing to follow these can result in severe penalties that could devastate any company.
- Targeting Financial Information: Like personal information, a small business also needs to take extreme care in storing customer financial information. Sensitive details like credit card or banking information are a prime target for hackers looking to steal money fast. The impact on your business reputation following a breach of financial data will be severe and devastating. Many fail to recover fully after losing the trust of their customers.
- Targeting Individuals via Social Engineering: Whether posing as a supplier, customer, or interested party, attackers can gain information that you wouldn’t want to hand over to a stranger. Small businesses are often used to gather information on their vendors and suppliers to source additional targets for cyberattacks. Be particularly cautious of the information you provide when discussing business with individuals you haven’t spoken to before.
Each of these targets and attacks are just some of the most popular and hard-hitting attacks out there now. Some can be defended against with great security, backups, and software. Others, such as social engineering, need you and your staff to stay up-to-date and remain vigilant about the major attacks affecting small business today.
Sounds scary, doesn’t it?
With the increasing number of connected devices in your business network and the different ways your employees now connect, it’s more important than ever to set up dedicated security systems that give integrated protection. We encourage you to download our resource of cybersecurity statistics covering the reach and consequences of cyberattacks.
Here’s four small steps your business can take starting today to provide stronger cyber protection.
Build a Robust Firewall
Put simply, a firewall keeps an eye on all the data coming in and out, looking for anything abnormal. It exists to make sure the data entering your network is safe, that it’s not part of a cyberattack, and that in the event your network becomes infected, your servers aren’t being used to attack another business.
Install Antivirus Software Where It Matters
With so much new malware being released daily, it’s easy to fall behind in updates and discover you’ve been infected. Your employees are likely doing their best, but manually scanning each file can be exhausting and time-consuming. With effective antivirus protection, malicious file don’t even make it to employees, so the risk is removed – keeping employees working effectively, and leaders running the business with confidence.
Set Up Spam Blocking
Most cyberattacks come via email these days, with either an attachment or a link. Once clicked, the malware is released into the network to wreak havoc. Hackers are clever and can often mimic email accounts used by company leaders or by familiar companies such as software providers or shipping companies. These emails look legitimate and may refer to vendors you use, financial services you have accounts with, or even seem to be from other employees.
With effective spam blocking software, anything suspicious is marked as spam and either held for review or bounced away. Employees will no longer have to spend precious time each day wading through the junk, and the threat of an errant click on a malicious email has greatly dropped. For spam emails that manage to evade your filters, training your team on the SLAM method adds another layer of prevention.
Enable Content Filtering
In a perfect world, your employees would only access work-related sites and do work-related things online. Content filtering can help you limit the risk they’re bringing into your business via these websites. It’s up to your policies how much you’d like to filter and whether to add any flexibility.
Systems are secure, employees can maintain efficiency in their normal working environments, and cyber problems stay outside the doors. The key is to layer solutions together to protect the points where the most common cyberattacks originate within your business. Our Small Business Guide to Cybersecurity is a great place to start building a strategy for mitigating cyber risk.
Can Your Small Business Take a Step Towards Better Cyber Protection?
With the threats of cyberattacks growing more and more each year, it pays to proactively invest in new protective measures, updates, and employee training. Cybersecurity doesn’t just come from massive firewalls and software programs, it also comes from sound habits and recognition of possible malicious activities. Take this checklist as a starter’s guide to improving your small business security!
The IT services team at Lighthouse Technology Services is here to help your business make sense of technology, find the best ways to utilize it, and ensure safe and productive work environments. Get to know our team and our work here, and feel free to contact us with any questions specific to your business.
For more great cybersecurity support for small and mid-sized businesses, check out this episode of Live With Lighthouse! Sedara Founder and CEO Darrick Kristich shares his expertise on building managed detection and responses programs that provide a more comprehensive 24/7 security view.





